How seriously does your organization consider cybersecurity as part of its business strategy?
The 9th edition of the State of Smart Manufacturing Report reveals that cybersecurity ranks third as an obstacle to growth, appearing in the top five for the first time. From this result, it’s clear that businesses need to improve the integration of cybersecurity within their IT and OT systems. Manufacturers are also already stepping up their technology investments by 30% to counter the risks of cybercrime, of which upskilling talent and hiring skilled employers are prioritized.
Additionally, in the 2024 State of Operational Technology and Cybersecurity Report by Fortinet, it is stated that 73% of OT professionals experienced intrusions that impacted their OT systems in some way. This is a stark increase from just 49% the year before. All of these point to an elevated need for cybersecurity awareness and action to mitigate the risk of cyberattacks.
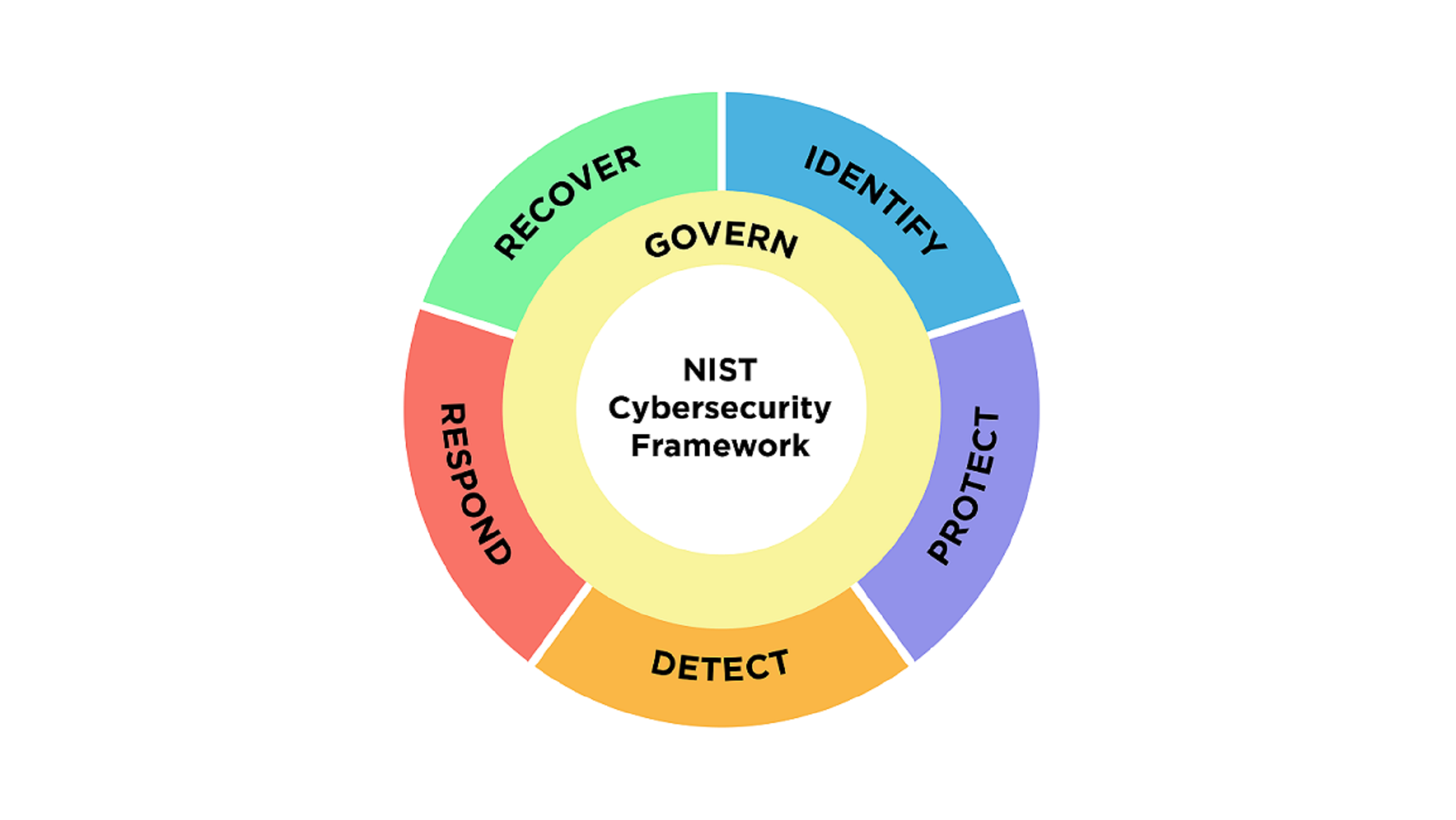
Addressing Cybersecurity through the NIST Cybersecurity Framework
To address these challenges, the National Institute of Standards and Technology (NIST) developed a cybersecurity framework that provides a structured approach to managing cybersecurity risks. First introduced in 2014 to support critical infrastructures, NIST released version 2.0 this year with a goal to broaden its use-case to be applicable across organizations.