All around we see technology adoption growing and accelerating across manufacturing and process automation, e-commerce supply chain, and distribution. Technology and automation can offset a manufacturer’s lack of access to skills and expertise, as well as labor shortages. They can also help a company achieve business goals around improving productivity, speed to market, sustainability, and safety. It's been reported that the Fourth Industrial Revolution technology advancements have accelerated per capita GDP growth at 20X …wow!
When you consider your digital transformation strategy and the investment to be made, cybersecurity should be a critical element to your investment, so that you can deploy networks that will perform for the long term while also being robust and secure from the threats of bad actors.
Here are some tips to consider when planning a cybersecurity strategy:
1. There is value in a Defense in Depth Strategy
Defense in Depth (DiD) is an approach to cybersecurity in which a series of defensive mechanisms are implemented to protect valuable data and information.
A good DiD strategy will include a thorough review of external and internal threat vectors as well as a best-in-practice approach to the logical network design, including:
- Utilizing the industrial security zone or iDMZ (industrial demilitarized zone)
- Computers and endpoint protection
- Authentication and authorization
- Common Industrial Protocol (CIP) security overview
- Asset management and recovery
- Patch management
- Secure remote access
- Industrial Control System (ICS) threat detection
- A planned logical network architecture such as the Converged Plantwide Ethernet architecture (CPwE)
For more tips on configuring your logical network when building a secure network infrastructure visit our webpage.
2. Insider Threats are Real
Insider threats are real. They could be current or former employees, contractors, or business associates. More than half of those surveyed by cybersecurity-insiders.com think it is more difficult to detect and prevent insider threats than external cyber-attacks.
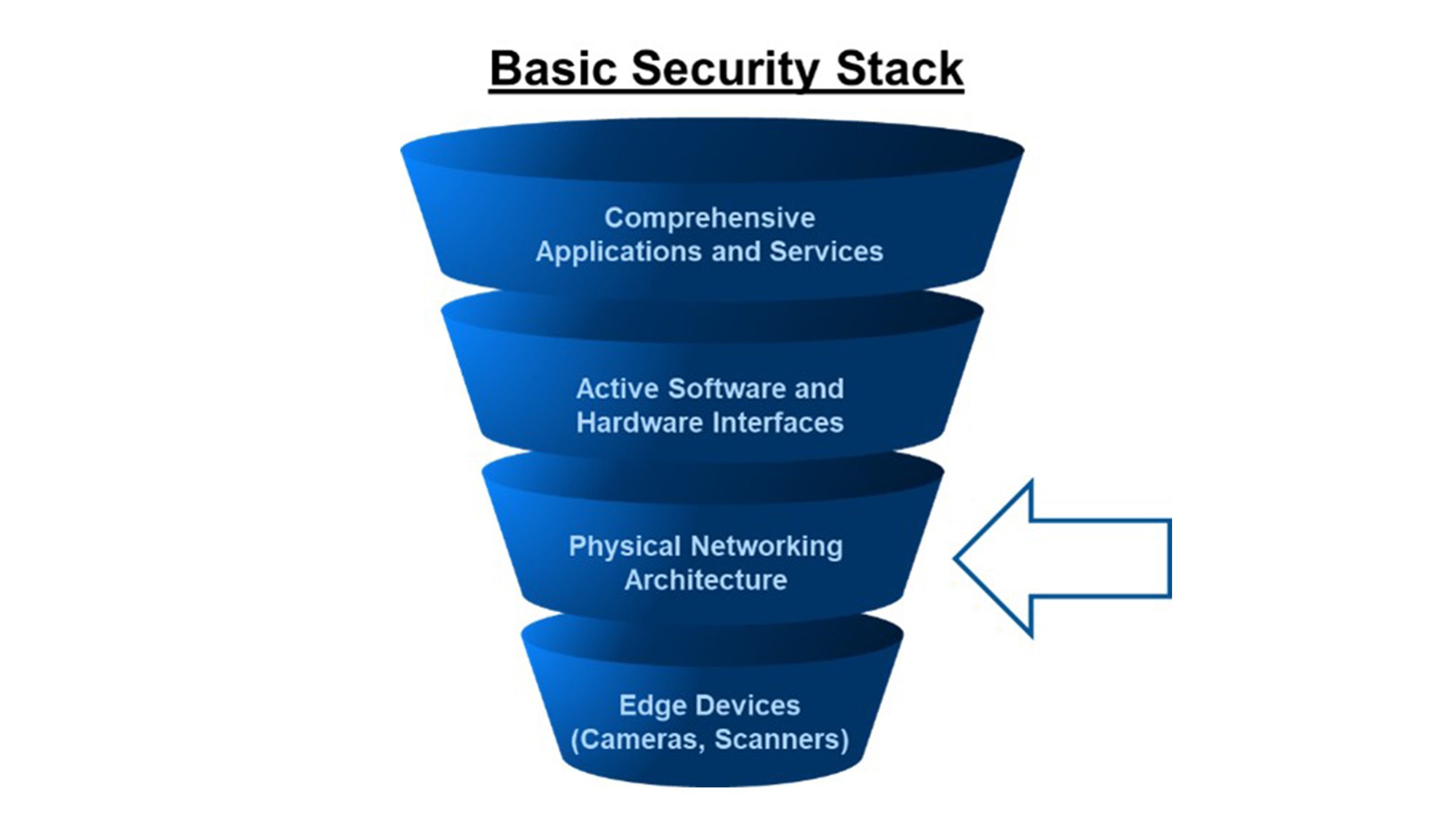
3. Physical Network Layer Planning is a Key Element of Defense in Depth
Physical layer planning provides a best-in-class execution plan for the network that can:
- Reduce vulnerabilities
- Enable controlled access to equipment to deter insider threats
- Contribute to more effective services to, and management of network hardware
A few areas where physical network design can improve overall security of the network:
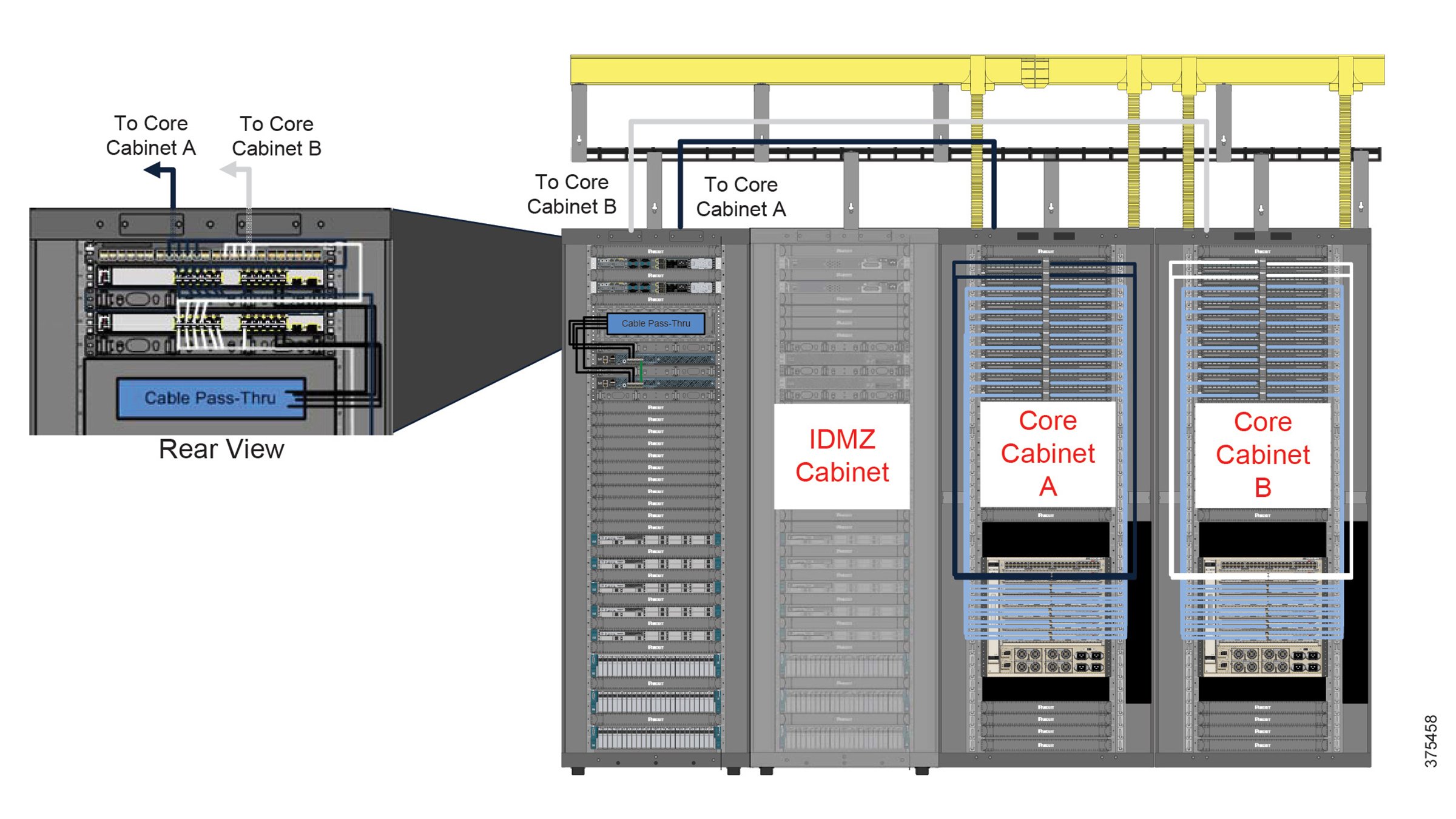
- Industrial compute platforms for deployment of iDMZ and security hardware
- Physical network segregation by cell zone areas, with switch distribution within zone or IDF enclosures to provide physical network isolation and limit threat impacts
- Equipment hardening and modern badged access control and lock security options at the enclosure level
- Access control integrated with safety protocols for control panels
- Physical port security – it is not enough to electronically lock down ports; physical port security physically blocks the port or locks a connection into the port to deter access
- Physical port security options:
- Port block-out and lock-in devices
- Lock in fiber uplink port connections
- Block out open USB and RJ-45 ports
- Physical port security options:
4. Cyber Security Standards
An understanding of important cybersecurity standards is required, along with access to design guidelines aligned to them. A few that are important to review:
a. Key standards NIST SP 800-82, ISA-99 and IEC 62443 series, Deploying Network Security within a Converged Plantwide Ethernet Architecture – DIG, and Physical Infrastructure for the Converged Plantwide Ethernet Architecture
- https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-82r2.pdf
- Understanding IEC 62443 | IEC
- https://literature.rockwellautomation.com/idc/groups/literature/documents/td/enet-td019_-en-p.pdf
- Physical Infrastructure for the Converged Plantwide Ethernet Architecture Application Guide ENET-TD020A-EN-P (panduit.com)
5. Getting Started on the Physical Network Infrastructure
Where do you start?
Begin with an evaluation of the overall network in place, looking for security vulnerabilities. A standard network assessment, available through Rockwell Automation, provides documentation of the major network components and a base line of physical, logical and security-based elements relative to industry standards. It has an expanded review of the physical network to ICT standards – important for IT managers – jointly created by Panduit and Rockwell Automation. It operates with minimal disruption to your production environment and includes a program report with recommendations and remediations.