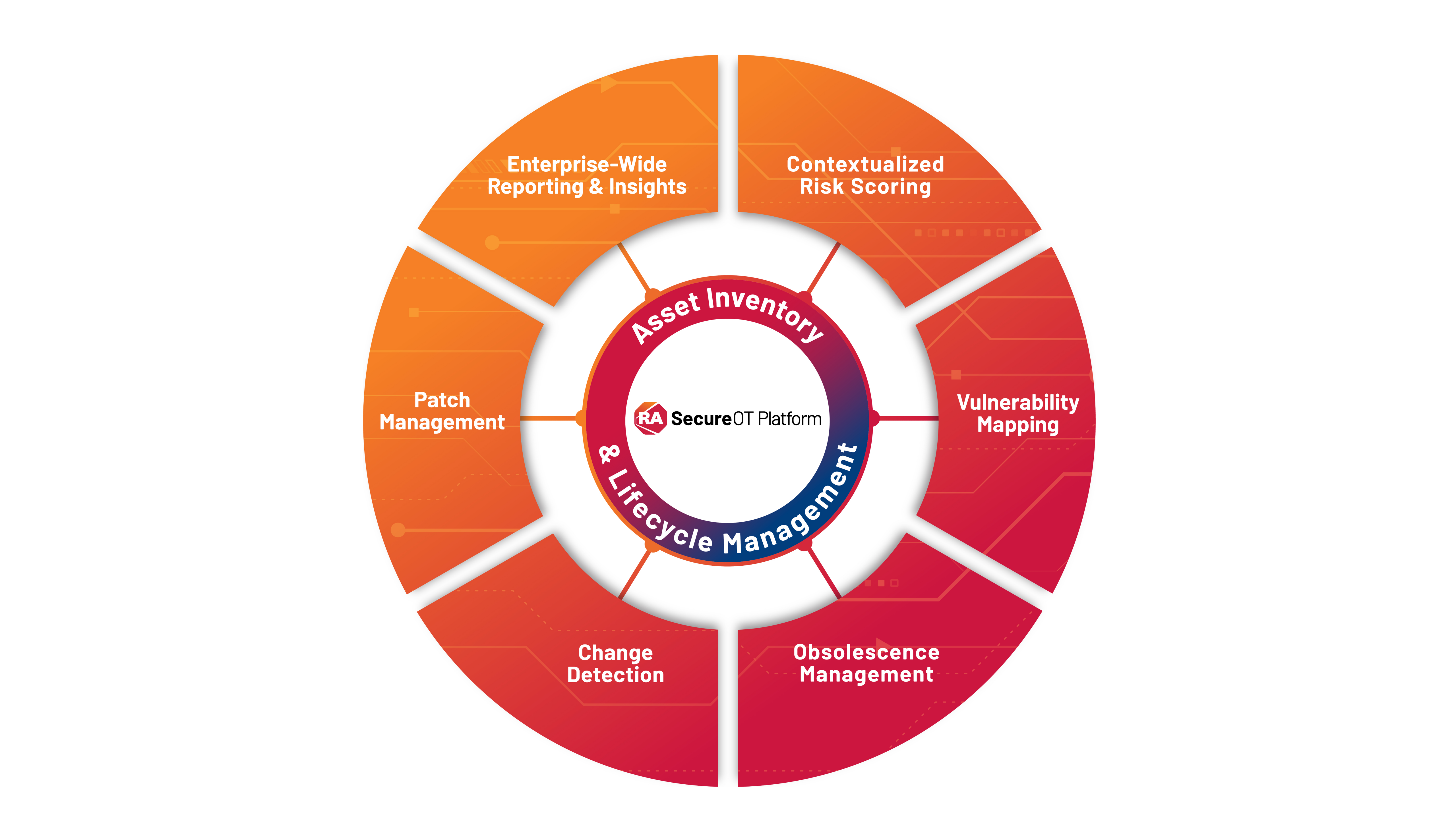
NIS2 Compliance for Manufacturing and Industrial Control Systems
NIS2 covers new sectors, including manufacturing, chemicals, waste management, and food production, among others. This is in addition to the sectors already covered by the first NIS, such as water supply, energy, and transport.