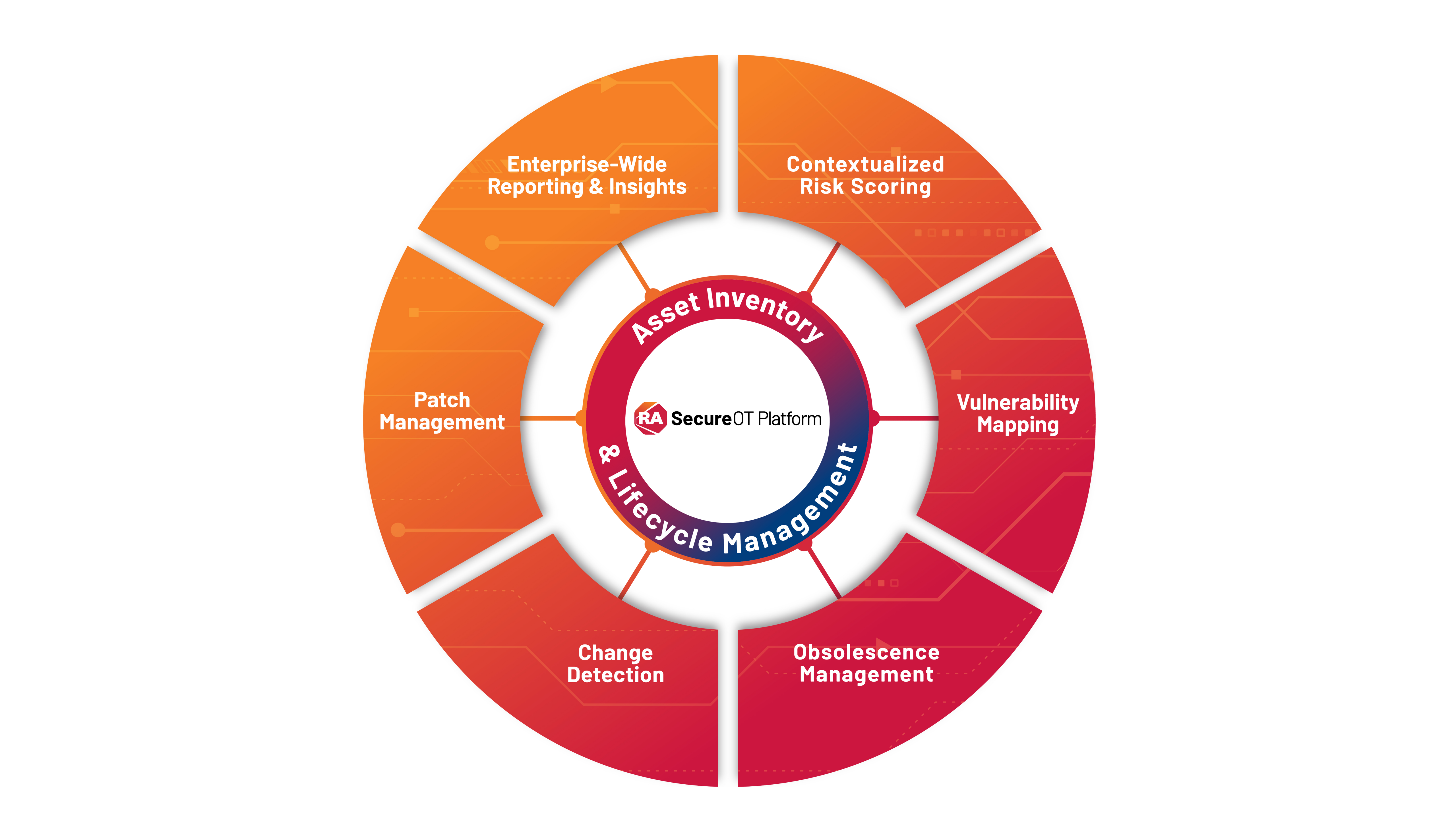
Your First Line of Defense Against OT Cyber Threats
Every day, OT environments face evolving cyber risks that target aging systems and complex networks. Managing these risks requires more than scanning. It demands a structured process to identify, prioritize, and remediate vulnerabilities before they disrupt operations. Traditional IT tools were never designed for this reality. They are intrusive, risky, and leave gaps that threaten uptime and compliance. SecureOT™ Platform solves these challenges with an OT-specific, closed-loop approach that strengthens resilience and helps keep operations running.