How networks and devices inherit security permissions
The security system applies inherited security permissions differently, depending on whether control hardware, available to a local computer through
RSLinx Classic
, is secured by a network relative path or a logical name, and depending on whether the device is a member of a resource grouping.How inheritance applies to network relative paths
Control networks and devices that are referenced by network relative paths inherit security permissions in the same way as any other securable resource. Security permissions are inherited from the resource and then up through the entire path to the network directory or local directory at the top of the
Explorer
.This means that control devices that are accessible through multiple paths can have multiple sets of security permissions.
How inheritance applies to logical names
Control networks and devices that are referenced by logical names inherit security permissions from only the logical name itself, then the top of the
Networks and Devices
tree, then the System
folder, and finally the network directory or local directory itself.When referenced by a logical name, a control device does not inherit security permissions from within the
Networks and Devices
tree.For example, if security is applied to controller 10.88.108.148,1756-ENBT, referenced by the logical name "ABC," shown below, then its security permissions chain equates to the following, even if security is also applied to the AB_ETH-1 network and to the Computer A workstation:
ABC > Networks and Devices > System > Network
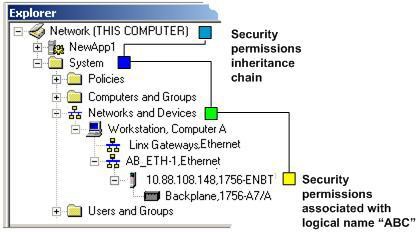
Unlike how inheritance works elsewhere in the system, security permissions for networks and devices that are referenced by logical names "skip" levels within the
Networks and Devices
tree. This prevents a single device from inheriting multiple sets of security permissions.The permissions inheritance chains for the networks and devices shown in the example above equate to the following, assuming that each is referenced by a logical name:
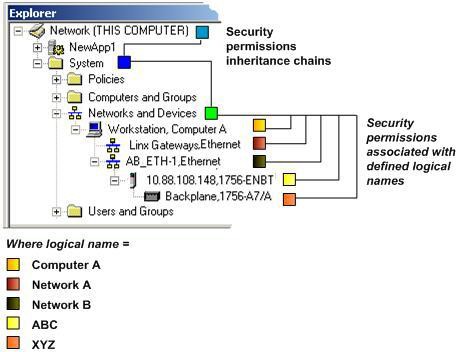
Network or device | Path of inheritance |
|---|---|
Workstations | Computer A (Workstation, Computer A) > Networks and Devices > System > Network |
Networks |
|
Controllers | ABC (10.88.108.148,1756-ENBT) > Networks and Devices > System > Network |
Backplanes | XYZ (Backplane, 1756-A7/A) > Networks and Devices > System > Network |
How inheritance works with and without resource groupings
A resource grouping allows the network or device to inherit its permissions from the application or area that the resource grouping is associated with, instead of inheriting its security permissions from the
System
folder, the Networks and Devices
node, and then the items within the Networks and Devices
folder, down to the device itself.This means that resource groupings allow networks and devices to inherit their security permissions just like any other resources located inside an application or area, simplifying administration.
If the network or device is a member of a resource group, and is also associated with a logical name, the device inherits its security permissions from the logical name and then from the application or area that the resource group is associated with.
In summary
- If a device has no logical name associated with it and is a member of a resource grouping, the path of inheritance for the device is:Device>area>application>Network Directory-OR-Device>application>Local Directory
- If a device does have a logical name associated with it and is a member of a resource grouping, the path of inheritance for the device is:Logical name>area>application>Network Directory-OR-Logical name>application>Local Directory
- If a device has no logical name associated with it, and is not a member of a resource grouping, the path of inheritance for the device is:Device>path through the Networks and Devices tree>Networks and Devices>System folder>Network or Local DirectoryInheritance does not skip any levels between the device and the top of theNetworks and Devicestree.
- If a device does have a logical name associated with it, and is not a member of a resource grouping, the path of inheritance for the device is:Logical name>Networks and Devices>System folder>Network or Local DirectoryInheritance skips all levels between the logical name and the top of theNetworks and Devicestree.
Remember that explicit permissions always override inherited permissions.
Evaluating access rights
The system checks security permissions for networks and devices in the following order:
- ExplicitDenypermissions are checked at the lowest level (for example, logical name "ABC," which references 10.88.108.148,1756-ENBT). If a matching entry is found, access is denied.
- Allowpermissions are checked at the lowest level. If a matching entry is found, access is granted.
- ExplicitDenypermissions are checked at the parent level (for example, theNetworks and Devicesfolder). If a matching entry is found, access is denied.
- Allowpermissions are checked at the parent level. If a matching entry is found, access is granted.
- If, after checking all levels, no matching permissions are found, then access is implicitly denied.
In this way, even though access may be explicitly denied at a parent level, the child level could override that setting and allow access. For example, overall permission to make ladder logic changes to
RSLogix 5
projects might be explicitly denied. However, the ability to make changes to a certain ladder folder in the project could be permitted.When permissions are evaluated, the lowest level is evaluated first, and then on up the chain.
Provide Feedback
