Why use a logical name?
Because
RSLogix 5000
controllers are identified by logical device names and not by relative paths. Define a logical name in FactoryTalk Administration Console
that maps to the controller's device name.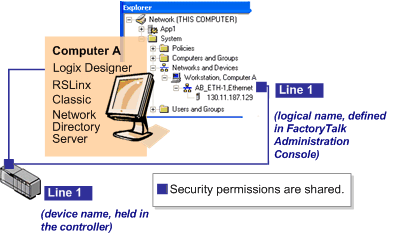
It is possible to define logical names as aliases for other types of control hardware with multiple paths, to associate each instance of the device with a single set of security permissions. Devices with identical logical names share security permissions across different control networks and across different computers.
For example, if a device is accessible from multiple control networks on the same computer, that single device appears in multiple places in the
Networks and Devices
tree, because the tree is populated based on relative paths. If security is configured for the device from one of its relative path locations, the security permissions are recognized only when the device is accessed from that path; they are not recognized when the device is accessed from a different relative path.In the example below, Computer A can access
PLC-5
130.11.187.129 from both an Ethernet network and a DH+ network. If security is configured for the PLC-5
from the Ethernet network, the PLC-5
is still unsecured from the DH+ network.However, if a logical name is defined as an alias for each instance of the
PLC-5
from the FactoryTalk Administration Console
, and security is configured for the PLC-5
, security uses the name to reference the security permissions, rather than the path. In this case, the device is secure, regardless of how it is accessed.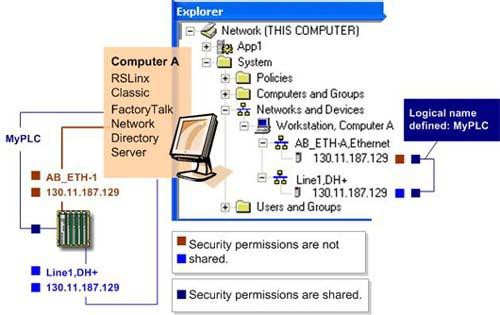
The same is true for a control device that is accessible from different networks on different computers. Suppose Computer A can access a
PLC-5
over both an Ethernet network and a DH+ connection, while Computer B can also access the same device over DH+. Using network relative paths, security sees this device as three separate entities. If security is configured for the PLC-5
from its DH+ network on Computer A, the device is still unsecured from its Ethernet network on Computer A and from its DH+ network on Computer B. However, if an identical logical name is defined as an alias for the PLC-5
from each of its locations on both Computer A and on Computer B, then the security configured for one instance of the device on one computer is shared across control networks and across computers.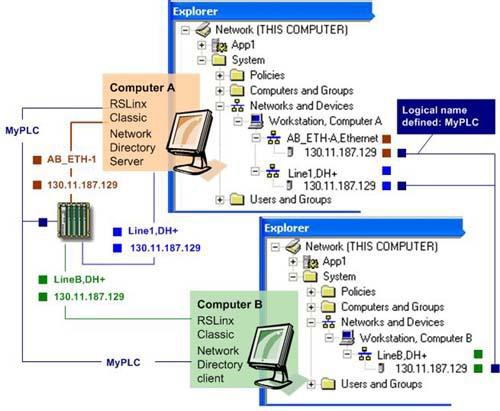
Provide Feedback
