Breaking the chain of inheritance
By default, resources inherit permissions automatically from their parent resources. For example, if assigning security to an area in an application, all of the items in the area inherit the security settings of the area, and the area inherits security settings from the application. The top of the hierarchy is the network directory or local directory.
Override inherited permissions in two ways:
- Set up explicit permissionsfor resources at a lower level of the hierarchy. For example, if an area inherits permissions from an application, override the inherited permissions by specifying permissions explicitly for the area.
- Break the chain of inheritanceat a level in the network directory or local directory tree. For example, stop an area from inheriting permissions from the application in which it is located by selectingDo not inherit permissionswhen setting up security for the area. When breaking the chain of inheritance, specify whether to remove all permissions from resources below the break (which then impliesDenypermission), or whether to use the permissions that are inherited by the resource at the break as explicit permissions.
Permissions are inherited only as far up the network directory or local directory tree as the chain of inheritance remains intact. For example, when
Do not inherit permissions
for an area is selected, items that inherit permissions inside the area can inherit permissions only as far as the area. They cannot inherit permissions from the application in which the area is located. Because breaking the chain of inheritance complicates administration, only do this when absolutely necessary.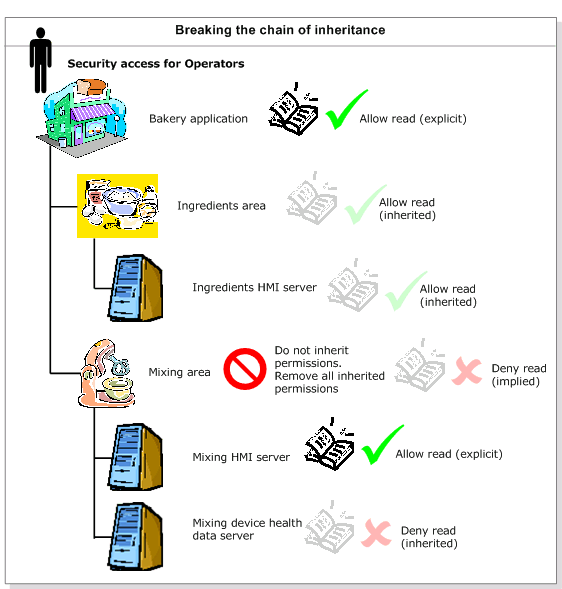
The principle of inheritance allows setting permissions at as high a level as is practical. Then, introduce exceptions at lower levels where necessary.
If permissions are not assigned at any level,
Deny
is implied.Provide Feedback
