Public Network with Reverse Proxy
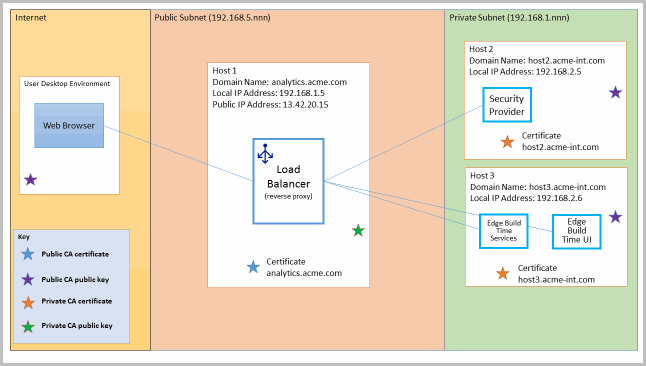
In this scenario all of the FactoryTalk Analytics applications are installed in a private subnet and a reverse proxy server (e.g. Apache HTTPD or NGINX) is installed in the public network. The proxy server redirects external requests to internal services hosted in the private network.
In this case the reverse proxy server should have a certificate signed by a commercial CA. The hosts in the private network should have certificates signed by the organization’s private CA. With all requests going through the reverse proxy, it is only necessary to share the public key for the private CA with the proxy server. The hosts on the internal network will need the public key for the commercial CA. It is likely that the CA’s public key may already be in the default Java truststore (ca certs), in which case trust with the proxy server will be automatic.
Public Network with Reverse Proxy
Provide Feedback
