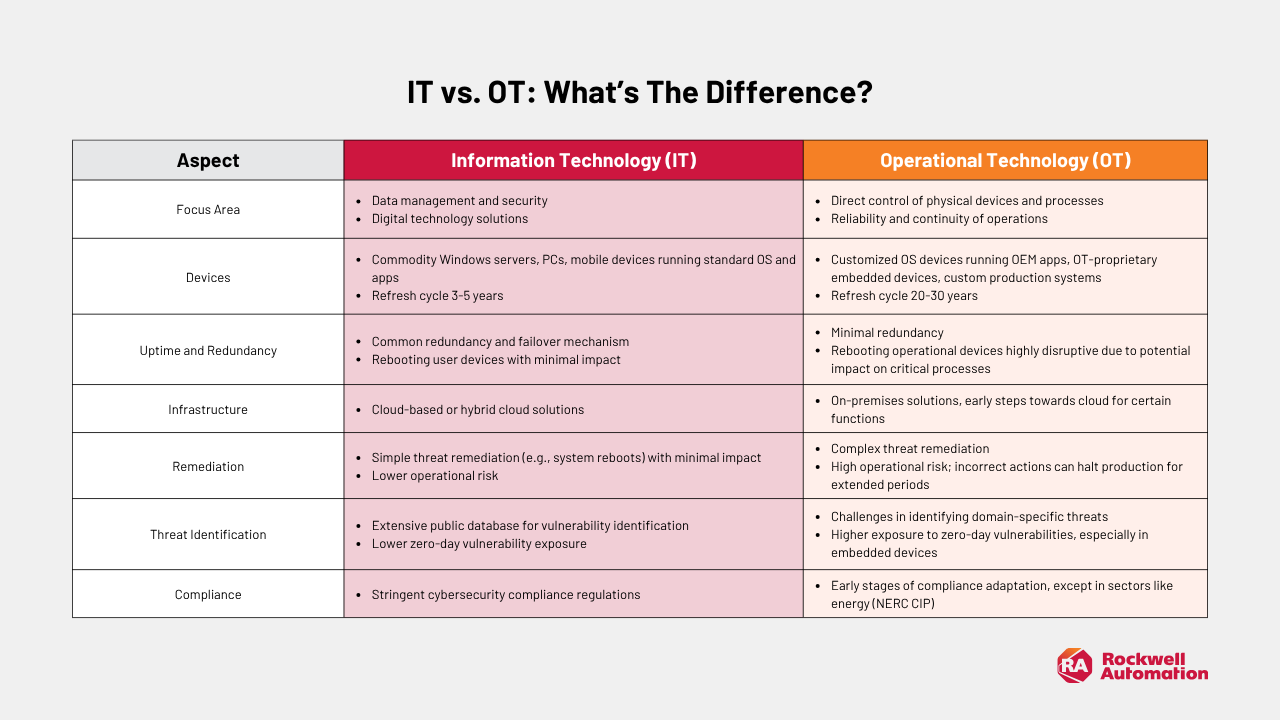
Attribute
|
OT Security
|
IT Security
|
Primary objective
|
Safety, Reliability, Availability (SRA)
|
Confidentiality, Integrity, Availability (CIA)
|
Typical system lifespan
|
15–20 years (or more)
|
3–5 years
|
Update cadence
|
Infrequent, carefully scheduled
|
Regular, often automated
|
Recognizing these differences enables teams to tailor protections to OT’s unique constraints—delivering safety and uptime without imposing IT-style change cycles that could disrupt essential operations.
Navigating OT Security Challenges
Organizations advancing OT security encounter several hurdles:
- Legacy systems – Aging equipment that can be difficult (and expensive) to patch or replace
- Continuous operation – Taking production assets offline for security work is often impractical
- Proprietary protocols – Many standard IT security tools don’t natively understand industrial protocols
- Diminishing air gaps – Expanded connectivity delivers value but also broadens the attack surface
- Skills gap – Effective protection requires expertise in both cybersecurity and industrial processes
Emerging Technologies Affecting OT Security
OT/IT convergence is reshaping industrial operations and introducing fresh security considerations. Key trends include:
Industrial Internet of Things (IIoT)
The IIoT connects sensors, actuators, controllers, and analytics platforms to unlock insights such as predictive maintenance. The same connectivity, however, increases risk when:
- Device counts surge, multiplying entry points
- Legacy assets—never designed for open networks—are brought online
- Security practices lag behind the unique requirements of OT
- Demand for professionals fluent in both automation and cybersecurity continues to outpace supply
Cloud Computing
Using cloud infrastructure can cut costs and speed deployment, but success depends on:
- Data security – Safeguarding sensitive operational data stored or processed off-premises
- Access control – Confirming only authorized personnel and applications interact with cloud-based OT systems
- Compliance – Meeting frameworks such as NIST SP 800-82 and IEC 62443 when workloads extend to the cloud
Artificial Intelligence and Machine Learning
AI/ML can strengthen detection and response by:
- Spotting anomalous patterns that signal emerging threats
- Predicting equipment failures to reduce downtime
Secure adoption requires guarding against issues such as data poisoning, model theft, adversarial inputs, and opaque decision-making. Robust data governance, model-protection controls, and explainable-AI practices help mitigate these risks.
Digital Twins
Digital twins are virtual replicas of a physical asset, system, or process. Drawing on real-time data from sensors and other sources, they mirror the original asset’s behavior, performance, and condition.
Security benefits include:
- Conducting attack simulations to test controls in a safe environment
- Identifying and addressing potential vulnerabilities before they affect the physical system
- Detecting behavioral anomalies that may signal a breach
5G
A 5G network delivers the high speed, low latency, and enhanced capacity required for real-time data exchange—and can even enable remote control of OT systems.
Security considerations:
- Expanded connectivity widens the potential attack surface
- Larger data flows raise the risk of breaches involving operational data, intellectual property, or customer information
- Supply-chain exposure to hardware, software, and services from third-party vendors must be managed
Edge Computing
Edge computing processes and analyses data close to its source, reducing latency and improving responsiveness. Securing large numbers of edge devices—often deployed in remote or harsh environments—means safeguarding the confidentiality, integrity, and availability of data processed at the edge.
Key Strategies for Robust OT Security
Comprehensive Asset Visibility
Building a detailed inventory of all OT assets—devices, hardware, software, and network connections—forms the foundation of a strong security program. Benefits include:
- Identifying vulnerabilities threat actors could exploit
- Prioritizing defenses around the most critical assets
- Improving response and recovery times during an incident
- Demonstrating compliance through an up-to-date inventory
How Asset Visibility Works
Just as a blueprint clarifies a building’s structure, asset visibility maps your cybersecurity landscape. Accuracy, completeness, and consistency are essential: maintain current information on every device, application, and connection.
Getting started
- Identify all OT assets.
- Categorize them by criticality and risk.
- Record detailed information for each asset.
- Update the inventory whenever changes occur.
Considerations and Best Practices
- Minimize disruption by collecting data during off-hours whenever possible.
- Select discovery tools compatible with existing OT protocols.
- Keep the inventory current when devices, software, or hardware are added or retired.
- Conduct regular vulnerability assessments.
- Align asset visibility processes with applicable regulations and standards.
Network Segmentation for OT
Network segmentation is the practice of dividing a network into smaller, isolated zones. This strategy minimizes the potential impact of cyberattacks and helps sustain operations.
Benefits
- Help protect your most critical systems while maintaining necessary access for authorized users
- Isolate high-priority OT traffic to optimize performance, improve operational efficiency, and keep critical data flowing
- Separate sensitive data and systems to meet industry regulations, streamline audits, and maintain compliance
- Keep critical OT systems online during a cyberattack—minimizing disruption and helping protect profitability
- Facilitate a more secure integration of new OT technologies and position operations for the future
How It Works
If an OT network is a city, segmentation creates neighborhoods with controlled entry points. Each zone receives security controls aligned to its risk level and function.
Key principles: intentional access, layered security, regular review, and collaboration. IT and OT teams must continually assess and adjust segmentation to match evolving operational needs.
Getting started
- Build a team with IT and OT representation
- Map the network
- Design the segmentation plan
- Deploy the plan—including testing and validated backup options
- Document, monitor, and adapt on an ongoing basis
Considerations and Best Practices
- Assess operational impact and limit downtime during implementation
- Confirm that segmentation does not degrade OT-system performance
- Begin with a well-defined risk assessment
- Implement segmentation gradually and iteratively
- Continuously monitor and evaluate effectiveness
Strict Access Control in OT Systems
Strict access control enforces rigorous authentication and role-based permissions so that only authorized personnel interact with critical OT systems. The core principle is the least privileged: users receive only the minimum access required for their roles.
Benefits
Helps reduce breaches, helps protects critical infrastructure, and supports system reliability.
How It Works
Securing access is akin to guarding a vault: authorized users possess unique keys, and their activities are logged and reviewed.
Getting started
- Identify users who need OT access
- Assign roles and define corresponding permission levels
- Implement multi-factor authentication
- Continuously monitor access and log activity
Considerations and Best Practices
- Balance strong security controls with operational requirements to avoid productivity slowdowns
- Use segmentation to limit lateral movement
- Enable multi-factor (and where practical, biometric) verification
- Regularly audit access logs to spot anomalies
OT-Specific Vulnerability Management
Vulnerability management is the process of identifying, prioritizing, remediating, and reporting software misconfigurations within OT systems. Because many OT assets run legacy software that cannot be patched on a typical IT cadence, this discipline is essential to reducing the likelihood of system failures and safeguarding critical infrastructure.
How Vulnerability Management Works
Vulnerability management resembles a routine structural inspection: identifying small faults early helps prevent major breakdowns later.
Getting started:
- Build and maintain a current inventory of OT assets.
- Apply a risk-scoring methodology and purpose-built OT tools to prioritize findings.
- Deploy patches, compensating controls, or other mitigations according to risk and maintenance windows.
Considerations and Best Practices
OT environments often cannot tolerate frequent reboots or extended downtime, so standard IT approaches rarely fit. Key points:
- Use assessment tools designed for industrial protocols.
- Align remediation with planned outages or maintenance cycles.
- Focus first on high-risk vulnerabilities; employ compensating controls when patching is not feasible.
- Document actions thoroughly to demonstrate compliance.
OT-Focused Incident-Response Planning
Incident-response planning prepares teams to detect, contain, and recover from cyber incidents quickly—helping prevent minor issues from escalating into serious disruptions and supporting operational resilience.
How Incident-Response Planning Works
Effective planning provides a clear playbook—much like a well-rehearsed emergency drill—so every stakeholder understands their role in a crisis.
Getting started:
- Perform regular, enterprise-wide asset inventories covering both IT and OT systems, noting which assets are network-connected.
- Implement continuous threat detection that flags deviations from normal operations.
- Establish and routinely exercise backup and recovery processes for critical applications and data.
Considerations and Best Practices
Challenges include limited visibility into legacy equipment and the need for tight coordination between IT and OT teams. Best practices:
- Integrate IT and OT response plans into a single, cohesive framework.
- Conduct realistic simulations to validate and refine procedures.
- Prioritize safe system recovery to minimize downtime while helping protect personnel and physical processes.
OT Security Awareness Training
Security awareness training educates employees and contractors about cybersecurity risks in OT environments. Because human error remains a primary cause of breaches, raising awareness helps curb phishing, accidental misconfigurations, and other preventable issues—while also improving cross-team communication.
How It Works
Like driver education classes, effective training equips participants to make safe decisions on the “road” of daily operations.
Getting started
- Identify topics most relevant to your organization.
- Tailor content to each role.
- Use real-world OT examples to keep learners engaged.
Considerations and Best Practices
- Ensure scenarios are OT-specific and reflect emerging threats.
- Address misconceptions about OT security early.
- Enlist leadership support to boost participation.
- Reinforce concepts through hands-on exercises, role-specific guidance, and ongoing refreshers.
Secure Remote Access for OT Systems
Secure remote access allows authorized personnel to reach OT assets from off-site locations—vital for maintenance and troubleshooting—while minimizing cyber risk.
How It Works
Grant time-bound access to the right person (or system) and monitor the session throughout:
- Establish a secure connection (e.g., VPN or zero-trust remote-access solution).
- Require strong, multi-factor authentication.
- Continuously monitor and log remote sessions.
Considerations and Best Practices
- Confirm compatibility with legacy systems before rollout.
- Filter network traffic and encrypt data end-to-end.
- Harden endpoints and keep them patched.
- Balance security controls with operational requirements to avoid unnecessary downtime.
OT Security Frameworks and Standards
Navigating the world of OT cybersecurity can be overwhelming due to the sheer number of different frameworks. Luckily, these frameworks offer guidance on building a strong security program. They cover both general OT security and industry-specific best practices. Some are mandatory regulations, while others are voluntary standards. Key frameworks include:
NIST Cybersecurity Framework
The NIST Cybersecurity Framework (CSF) provides guidelines for organizations to proactively manage cybersecurity risks, identify vulnerabilities, and effectively respond to incidents. Organizations can pair this broader framework alongside the niche NIST 800-53 catalog for a comprehensive OT security strategy.
- Who developed it: The National Institute of Standards and Technology (NIST)
- Who it’s intended for: All organizations, including those with ICS and IoT devices
- Structure: NIST CSF offers around 120 detailed subcontrols with five key areas covering everything from technical defenses to processes and procedures.
- Goal of framework: Provide a flexible and customizable approach to managing cybersecurity risk.
Example Scenarios of NIST Cybersecurity Framework in OT
A water treatment facility uses NIST CSF to improve its cybersecurity awareness training program. As a result, the employees are more educated about the risks of phishing attacks and engineering.
CIS Top 18 Security Controls
The Center for Internet Security Controls (CIS) is a prioritized list of cybersecurity best practices that help organizations protect their systems and data. Initially focused on IT environments, CIS now includes an OT version that addresses the unique challenges of industrial systems.
- Who developed it: The Center for Internet Security (CIS) created this framework in coordination with the US DHS, NSA, SANS, and more.
- Who it’s intended for: Industrial organizations
- Structure: CIS controls include over 18 critical security controls that guide organizations in identifying, protecting, detecting, responding to, and recovering from cyber threats.
- Goal of framework: Improved operational reliability, safety, and business continuity
Example Scenarios of CIS in OT
An energy plant uses vulnerability management controls to identify and address outdated firmware on critical equipment. The result of these efforts is enhanced visibility of OT assets and improved resilience against cyber threats.
NIST 800-53 and Sub-Standards
NIST 800-53 provides a comprehensive catalog of security and privacy controls for industrial control systems. Organizations can use this technical framework alongside the broader NIST Cybersecurity Framework (CSF).
- Who developed it: The National Institute of Standards and Technology (NIST)
- Who it’s intended for: Federal agencies, but it’s widely adopted by other industrial organizations.
- Structure: NIST 800-53 has over 1,000 controls within 18 families, including Identification and Authentication, Access Control, Risk Assessment, and System and Communications Protection.
- Goal of framework: Provide organizations with detailed guidance in selecting and implementing appropriate security controls to protect their systems and information.
- Obstacles: Integrating technical controls and modern security practices to limited capacity, legacy systems.
Example Scenarios of NIST 800-53 in OT
A manufacturing plant uses controls from the Identification and Authentication family to confirm that only authorized personnel can access critical systems.
ISO 27000 Series
The ISO 27000 series provides best practices for managing information security. Robust information security practices are crucial in OT environments because they help protect sensitive data often used by OT systems, provide flexibility on how to implement the standard, and build a culture of security across your organization.
- Who developed it: International Electrotechnical Commission (IEC) and the International Organization for Standardization (ISO)
- Who it’s intended for: Any organization in any industry but still has relevance in the OT environments.
- Structure: Key standards include 1) ISO 27001, which outlines the standards for Information Security Management Systems (ISMS), and 2) ISO 27002, which offers recommended security practices.
- Goal of framework: Establish a robust and systematic approach to strengthen risk management and improve regulatory compliance.
- Obstacles: Adapting the ISMS model to OT systems can come with operational constraints (i.e., downtime).
Example Scenario of ISO 27000 in OT
A manufacturing plant implements an information security management system based on ISO 27001 to identify vulnerabilities within its production line. They implement access control measures per ISO 27002 to restrict access to critical systems and data. Implementing both standards improves the plant's security and reduces the risk of cyberattacks and data breaches.
IEC 62443 and ISA 99 Standard
IEC 62443/ISA 99 is a security standard designed explicitly for OT environments that provides a framework to protect industrial systems against cyberattacks.
- Who developed it: Joint effort from the International Electrotechnical Commission (IEC) and the International Society of Automation (ISA)
- Who it’s intended for: Manufacturing, energy, and utilities organizations
- Structure: There are four categories of standards with tiers of security to protect against attacks (segmentation, secure design, and lifecycle management). These standards also include technical security requirements for system integrators and operators.
- Goal of framework: Provide a comprehensive set of cybersecurity requirements for industrial automation and control systems (IACS).
- Obstacles: Implementing IEC 62443 can be resource-intensive and complex, especially for organizations with older systems.
Example Scenario of IEC 62443/ISA 99 in OT
A manufacturing plant implements IEC 62443 by defining security zones within its industrial network to isolate critical systems such as robots and programmable logic controllers (PLCs). This network segmentation helps limit the impact of potential cyberattacks by containing the spread of malware or other threats.
The plant also integrates security considerations into the development lifecycle of all new OT devices to ensure that security measures are built from the ground up. These actions result in enhanced system security, reduced attack surfaces, improved resilience to cyber threats, and enhanced compliance with relevant regulations and industry standards.
Building an OT Security Program
OT personnel balance evolving cyber threats, the convergence of IT/OT practices, and shifting regulations. This heightened risk demands a comprehensive approach to OT security—mirroring the robust measures already proven in IT environments.
Regulations such as the TSA pipeline requirements and NERC CIP standards push organizations to know more, act quickly, and report in new ways. Adapting to these mandates is resource-intensive, especially for OT environments with limited staff and downtime windows.
Core Elements of a Successful Cybersecurity Program
- Align with a recognized framework—for example, the NIST Cybersecurity Framework or IEC 62443—that enables clear measurement and tracking.
- Conduct a comprehensive review of your assets (patch status, vulnerabilities, user accounts, and more) to establish an accurate risk picture.
- Develop a proactive OT-security roadmap with layered defenses that span endpoint and network controls.
- Create repeatable OT security management processes and collaborate with IT to identify alignment opportunities.
- Integrate security metrics into performance targets, so departments are accountable for remaining within approved processes.
Dive deeper: Watch our webinar The Future of OT Security: Emerging Trends for a detailed walkthrough of this strategy.
The Future of OT Security: Emerging Trends
Conclusion: The Imperative of OT Security
Cyber threats continue to evolve and increasingly target industrial systems. Robust OT security safeguards physical assets, maintains operational continuity, and protects public safety. Achieving this requires an up-to-date asset inventory, continuous security monitoring, regular testing, and close alignment with IT.
By addressing the unique challenges of OT and applying the strategies and frameworks outlined here, organizations can strengthen their resilience and protect the integrity of critical operations.